Patch Management – why your business needs it
What is it?
Let’s take this step by step. A patch is a piece of computer code or some files that patch up a problem by updating, fixing or improving it. Windows Updates are often referred to as patches. You will get a Windows Update because Microsoft has found a security issue that needs fixing. In other words, they have found a hole and need to patch it! The update/patch copies new files to your computer or adds some new coding and voila the issue is dealt with and your computer is no longer at risk. Patch Management is the process of managing these patches/updates on your network.

Why do I need Patch Management?
As you can imagine, because of the number of security threats – there is a lot of updates to cope with. Microsoft is not the only manufacturer to release updates. All good software houses will release updates for their products.
As soon as a patch/update is released, the security hole becomes public knowledge. Public knowledge means very bad, but very clever attackers can rush to exploit it. You should apply updates as soon as you can to mitigate this opportunity for cyber criminals. You should also be aware that to be fully GDPR compliant, you need to do your best to protect your data. One way to help with this is to put in place a good Patch Management policy/procedure.
A good way to picture it: if you’re a visual person like myself, imagine yourself maintaining a car. Without regular services, changing your tyres etc… you can still drive your car. If you keep avoiding the mechanic, eventually the car will break down or cause an accident. It’s the same with Patch Management – you can go on without doing all your updates for a while and you’ll still be able to use your computer. However, without regular updates/maintenance, your device will become unprotected and potentially dangerous.

Patch Management Software
Because of how many malicious attacks that software companies face on a regular basis – there is lots of patches to deal with on one device, no matter a full office worth. Thankfully, there are some wonderful people out there that recognised this and developed software to deal with all of the patches/updates for you. Meaning that you can get on with all the other important things on your to-do list.

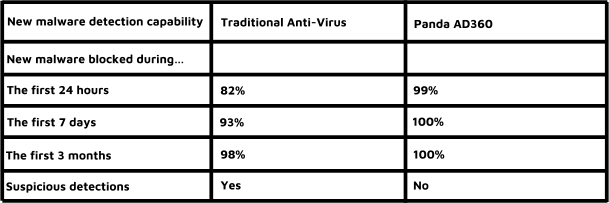
We recommend Panda Patch Management which has the ability to manage your network from one device, which can be a chosen person at your office or we can manage it for you here at Castle Computers.
Contact us on 01228 590900 or email info@castle-computers.com for more information on this software. We’re happy to answer any questions you have!